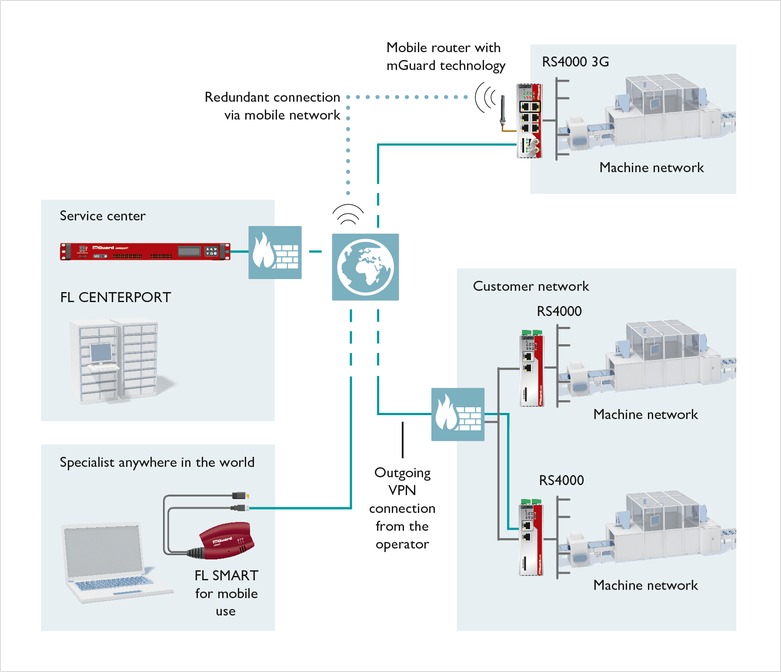
VPN
Via open Internet connections, criminals can copy data or make changes to the system. Using firewalls, the access to automation systems from the external networks can be restricted to authorized connections. In addition, remote connections via the Internet should always be encrypted, for example via a virtual private network (VPN).
VPNs are a protective measure to prevent unauthorized access to your network, e.g. for remote maintenance access. Protocols used to establish a VPN do not only secure against interception or eavesdropping, but also contain mechanisms to protect against manipulation.
For securing networks via VPN, Phoenix Contact offers the mGuard product line as a security appliance. Other products (e.g., PLCnext Technology controller) may also come with built-in VPN support. Refer to the current Phoenix Contact product catalog (phoenixcontact.net/products).