AXC F 3152
There are different Ethernet and firewall configurations due to three Ethernet interfaces.
Connecting and operating elements
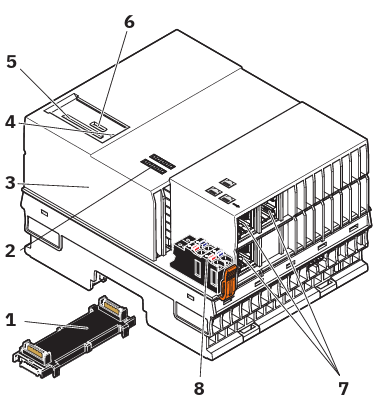
The controller consists of the following components:
| 1 | Bus base module |
| 2 | Diagnostic and status indicators |
| 3 | Electronics module |
| 4 | Reset button |
| 5 | SD card holder |
| 6 | Service interface (X4) |
| 7 | Ethernet interfaces (X1, X2, X3) |
| 8 | Supply connector (connector for connecting the supply voltage (communications voltage UL)) |
SD card
- Only use encrypted SD cards!
Information on this can be found in the topic SD card encryption.
Security seals
In order to prevent manipulation of the device supplied and to detect unauthorized opening of the device, security seals have been applied to the controller.
From hardware revision 04, the housing of PLCnext Control AXC F 3152 is protected by security seals like shown below.
These security seals are damaged in the event of unauthorized opening. In this case, correct operation of the PLCnext Control can no longer be ensured.
- Check the delivery for transport damage. Damaged packaging is an indicator of potential damage to the device that may have occurred during transport. This could result in a malfunction.
- Do not open the housing. If the housing is opened, the function of the device can no longer be ensured.
- Check at regular intervals that none of the seals are damaged. If any of the seals are damaged or missing, it may be that the device has been tampered. In this case, contact Phoenix Contact without delay before using the device.
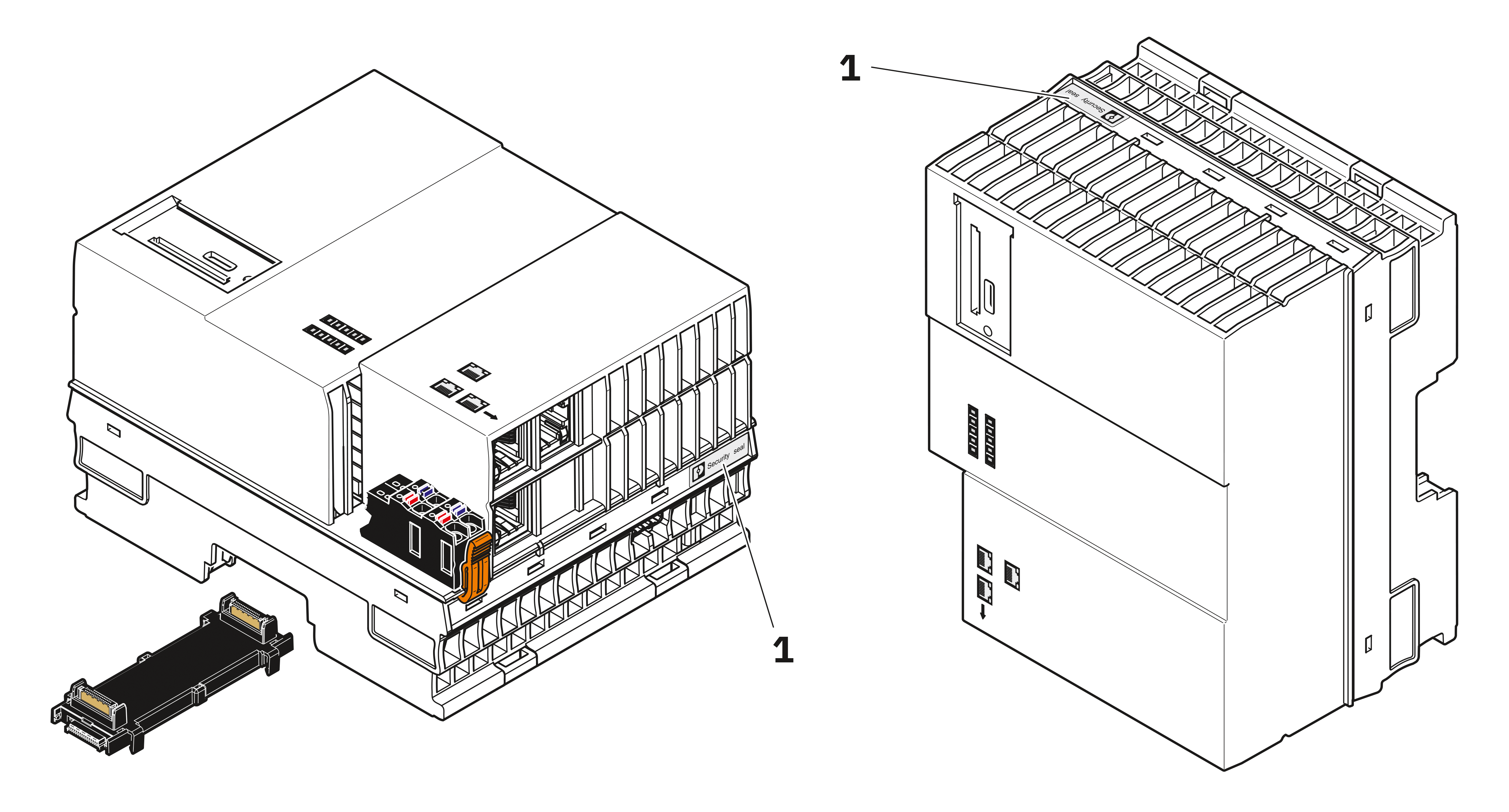
1 Security seals
Checking the device identity
PLCnext Control uses Trusted Platform Modules (TPM) to ensure the device identity. During production, a unique Device Certificate (IDevID) is installed on each device and stored in the TPM. To check the device identity, please check the device certificate and follow the certificate chain to the Phoenix Contact root certificate. Depending on the controller model or hardware revisions, PLCnext Control devices use different types of TPMs.
Latest AXC F 3152 hardware revisions are containing the Infineon Trusted Platform Module 2.0 SLB 9673 (firmware 26.13). The compliance with FIPS 140-2 physical level 3 is confirmed by NIST CMVP certificate #4467.
Activating PROFINET
After you have performed a threat analysis and implemented appropriate protective measures from the security context, you can activate PROFINET.
For information on how to activate PROFINET, refer to the topic Activating PROFINET in this PLCnext Technology ‑ Security Info Center.
For further information on PROFINET in the WBM, refer to the PROFINET diagnostics topic in the main PLCnext Technology ‑ Info Center.
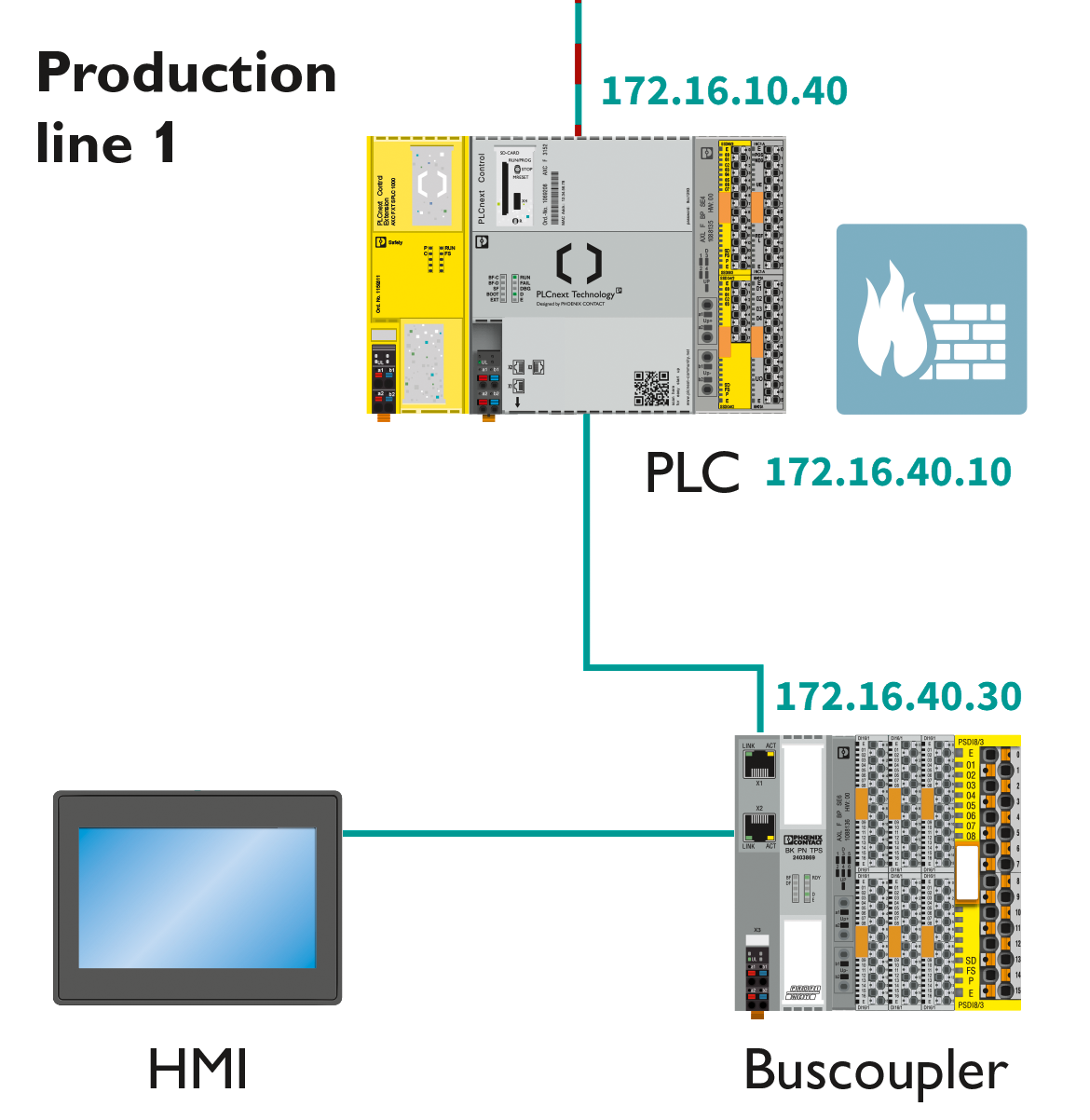
Using PROFINET
Communication paths
The controller consists of these communication paths:
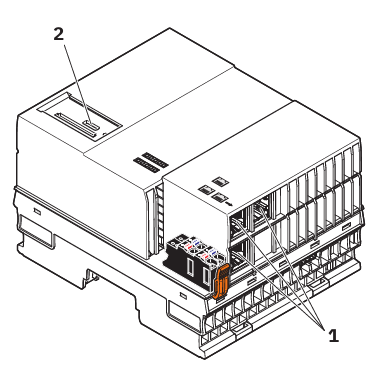
| 1 | 3 x Ethernet | X1/X2/X3: 10/100/1000 BASE-T(X) |
| X2: PROFINET controller interface | ||
| X3: PROFINET device interface | ||
| 2 | Service interface | For service purposes, you can connect a PC to the service interface (USB-C interface). In this case, the service interface is used as an Ethernet interface (default IP address: 128.0.0.1/30). Use as a USB host interface is not possible. Note: The service interface is deactivated by default. Perform a threat analysis before activating the service interface! The procedure for commissioning the service interface can be found in the topic Starting up the service interface of the AXC F 3152 in the main PLCnext Technology ‑ Info Center. Only operate the service interface within the protected network! The service interface must be secured via the firewall (as described below)! |
Ethernet interfaces
The Ethernet interfaces are assigned as follows:
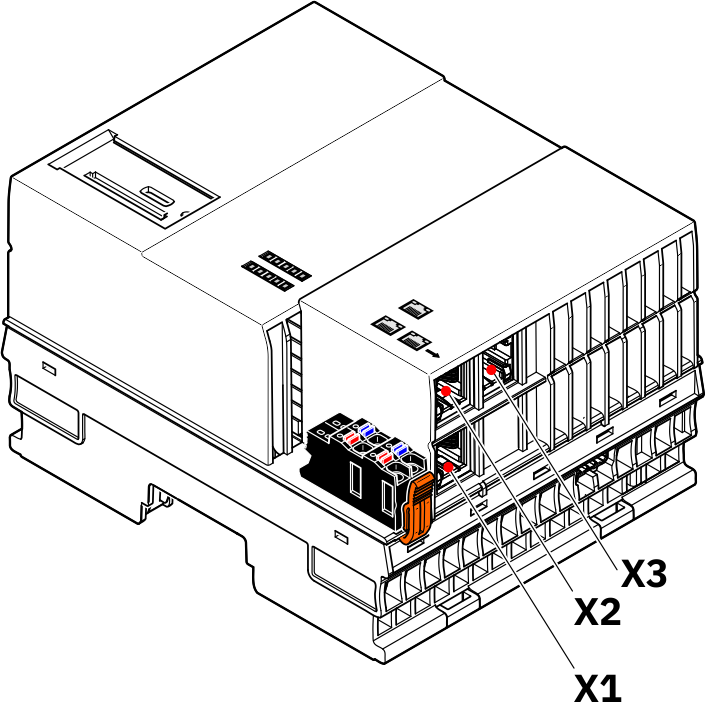
Assignment of the Ethernet interfaces
The following is an overview of how the Ethernet interfaces are assigned on the various pages in the WBM:
| Ethernet interface hardware | Ethernet interface WBM - Network page | Ethernet interfaces WBM - Firewall page |
| X1 | TCP/IP (LAN1) | LAN1 |
| X2 | TCP/IP (LAN2) | LAN2 |
| X3 | TCP/IP (LAN3) | LAN3 |
Firewall configurations
You need to adjust the firewall configurations (for more information, refer to the firewall basic configurations ):


Using the service interface (USB)
- Perform a threat analysis before activating the service interface.
You should only use an SSH connection during commissioning, not during operation of a system.
Here is an example of the firewall settings you need to make when using the service interface (see comments in the following screenshot):

How to reset the controller
Reset 1
Resetting the controller to default setting type 1 deletes all settings that you have configured. These include, for example:
- The PLCnext Engineer project, including all applications that have been programmed in accordance with IEC 61131-3
- All applications that were programmed using high-level languages
- The configured bus configuration
- The network configuration of the controller
- Changes and extensions that you have made to the operating system or to the firmware
To reset the controller to default setting type 1, proceed as follows:
- Switch off the supply voltage of the controller.
- After the LEDs have gone out, press the reset button.
- Hold the reset button down and switch the supply voltage on.
The RUN and FAIL LEDs light up. - Release the reset button.
The controller is reset to default setting type 1.
Reset 2
Resetting to default setting type 2 resets the controller to the delivery state. This deletes all settings that you have configured.
To reset the controller to default setting type 2, proceed as follows:
- Switch off the supply voltage of the controller.
- After the LEDs have gone out, press the reset button.
- Hold the reset button down and switch the supply voltage on.
The RUN and FAIL LEDs light up. - Press and hold the Reset button down (approx. 30 s) until all LEDs (except the E and D LEDs) light up.
- Release the reset button.
The controller is reset to default setting type 2.
Netload Limiter configuration
You configure the Netload Limiter on the Netload Limiter page in the WBM (Configuration → Network, Netload Limiter tab).
The Netload Limiter must be activated on the interface x1 (LAN 1).
For further information, refer to the topic Configuring Netload Limiter.
Controller-specific information on the 62443-4-2 compliance list