Network segmentation
It is difficult to determine the protection needs of an entire plant and to implement protective measures on this basis. If an office network, factory network and, for example, production line networks are directly connected to each other, malfunctions and viruses can be spread directly over all network parts. Network segmentation eliminates the risk that any data can directly be transferred between external networks or, e.g. the office environment and the production area/ICS networks.
The IEC 62443 standard divides a complete system into so-called zones and conduits. In practical implementation this means that the network to be protected must be segmented. The resulting network segments (cells) as well as the data paths between them can then be protected by targeted security measures.
Zones, cells, segments
In terms of the standard, a zone can be a physical and/or logical group of system components to which the same security requirements apply.
However, for the purposes of this manual, we look at segmentation a little differently: We divide the entire plant into segments/cells that are physically connected to each other and form a physical zone, so to speak. Each of these cells has a specific protection need.
Deviating from the IEC 62443 standard, we consider only such cells to be zones, although the standard also defines purely logical groups as zones.
If we look at the specific (technical) security measures to be implemented, these are generally limited to physical network segments (cells). Since we equate cell = zone, the required protection measures are easier and more clear to implement. As a result, we may get several cells (= zones) with the same protection need (security level) although the standard would comprise them into one zone.
Requirements and general considerations
The operator of an ICS must ensure that segmentation and communication policies are established and implemented for the interconnection of networks from the ICS and other networks. This is because external networks are a threat to the ICS as they allow access from potentially unknown sources.
The segmentation of networks allows to restrict data and control flows as well as the visibility between the ICS and external systems. The plant operator should identify, manage, authorize, and document all connections between the ICS and external systems.
Only the data flows that are necessary should be allowed. In the context of network segmentation, the connections between segments must be examined for threats and the associated risks. The documentation to be prepared must note these security risks and their designation as trustworthy or non-trustworthy. For non-trusted connections, a high level of protection is required. Identifying the non-trusted connections is a fundamental step in establishing network access controls.
If a functional safety system network is integrated in the ICS, the plant operator must ensure that the safety system is not affected by non-safety (i.e., standard) system networks and devices. To protect the safety system from interference, for example, firewalls or gateways can be used to manage access to the safety system. This way, a certain separation between the (standard) control system and the safety system can be realized.
The resulting segments can be separated using VLANs or firewalls. Routers or Layer 3 switches then need to be used for communication between the individual network segments. These devices intercept typical network errors, preventing them from spreading further to the rest of the network.
Separation: OT (ICS), IT and cloud
Details on the differences between IT and OT (ICS) networks can be found in IT and OT/ICS: A Comparison.
The following figure shows an example where mGuard security routers handle the communication between network segments.
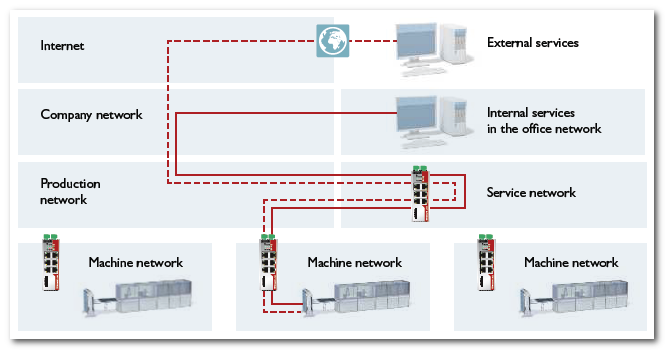
Rules for network segmentation
According to the IEC 62443 standard, the following rules apply when segmenting the ICS into zones and conduits:
- According to "FR5 - Restricted data flow", zones and conduits must be defined in such a way that unnecessary data flow is prevented.
Depending on the security level (SL 1 to 4), the casual/coincidental or intended circumvention of the defined zone and conduit segmentation must be prevented with the means, resources, skills and motivation as defined in the SL classification table. - Conduits should control the information flow and separate the ICS from public networks.
- Network components which represent a zone border must be able to protect the zone.
At zone borders, which represent the transfer point between a zone and a conduit, only network devices should be used which are able to protect the zone border by monitoring and controlling the inter-zone communication (represented by a conduit).
These are mainly devices with managed interfaces such as firewalls, encrypted tunnels, routers, proxies, (unidirectional) gateways.Note: Also dual-homed devices (PCs, controllers etc.) should be considered. Such devices have two network interfaces and they are part of two networks at the same time. In this architecture, these devices can form (unintentional) conduits and become (undetected) security risks.
Possible measures for implementation
Possible measures to protect zones and secure interzone communication:
- Firewalls
- Determine communication relations according to the least privilege concept: The default is "deny" and only needed communication relations should be explicitly allowed.
- Routers or Layer 3 switches handle the communication between network segments
- Prohibition of uncontrolled access
(e.g. mobile routers) - Isolation/separation from the Internet
- No routing of DNS requests to the Internet
- No default route
- Use of a Web Proxy
- Locks with exceptions (for pass)
- Network Address Translation (NAT)
- Port Forwarding