Security Profile: PLCnext Technology security hardening
To use PLCnext Technology as an IEC 62443-4-1/4-2 certified component, the activation of the Security Profile is mandatory. In addition, the automation system design must fit the security context and the generic use cases described in this PLCnext Technology ‑ Security Info Center.
With activated Security Profile PLCnext Technology supports the following functions:
- Clean device (Reset type 1)
- Integrity check on boot
- Least functionality
- Limited PLCnext Technology openness
- Only dedicated PLCnext ARP modules loaded
- No root access, no SSH access,
adminuser switched off
- Authorization
- Password complexity rules, lifetime restrictions and timeouts (brute force protection)
- Specialized
SecurityAdminandSecurityAuditoruser roles for device configuration and security monitoring - Central User Management systems support via LDAP
- Zone and denial of service protection
- Firewall configuration for each dedicated Ethernet MAC address via WBM
- Validation of incoming and outgoing data via external interfaces
- Netload Limiter pre-configured and configurable
- Certificate Authority (CA) manages device identity and trusted partners
- Integrity and authenticity of data in rest and data in transmission
- SD card with encrypted partition
- Secure communication TLS 1.2, TLS 1.3 and OPC UA® (signed & encrypted)
- Security logging
- Protected security logging
- Connection to a central server
- Explicit activation of PLCnext Technology features via WBM
- eHMI, or OPC UA®
- App Manager for using the PLCnext Store might be activated (according to the security context, a threat analysis required)
- Local Axioline I/Os are supported
- PROFINET can be activated after threat analysis and protection measures from the security context
- Cabinet supervision (must be locked) via an application which generates security notifications
For more information on these features, please refer to the IEC 62443-4-1/4-2 Security Level 2 (SL2) feature set described in the IEC 62443-4-2 compliance list.
Security architecture
To fulfill the IEC 62443-4-1 requirements a threat analysis of the PLCnext Runtime System and PLCnext Technology hardware is an important task. The PLCnext Technology threat analysis is based on the STRIDE model which consists of the identification of these security threats in these categories: spoofing, tampering, repudiation, Information disclosure, denial of service, elevation of privilege.
As a prerequisite the security context defined in this PLCnext Technology ‑ Security Info Center and the implemented Security Level 2 (SL2) feature set are used.
One key element of the threat analysis is to review the integrity and authenticity of the data in rest and data in transmission. Another key element is the authorization of human users and software components to access the data. In addition, the firewall protects the access to the communication interfaces, or supports denial of service protection.
PLCnext Technology provides TLS 1.2 or TLS 1.3 based communication on necessary communication interfaces (e.g. HTTPS, OPC UA®, PLCnext Engineer).
For other communication channels like LDAP or Syslog-ng, TLS can be activated according the users’ needs.
The authorization is handled by an RBAC user management for human users, and/or certificate management for software components.
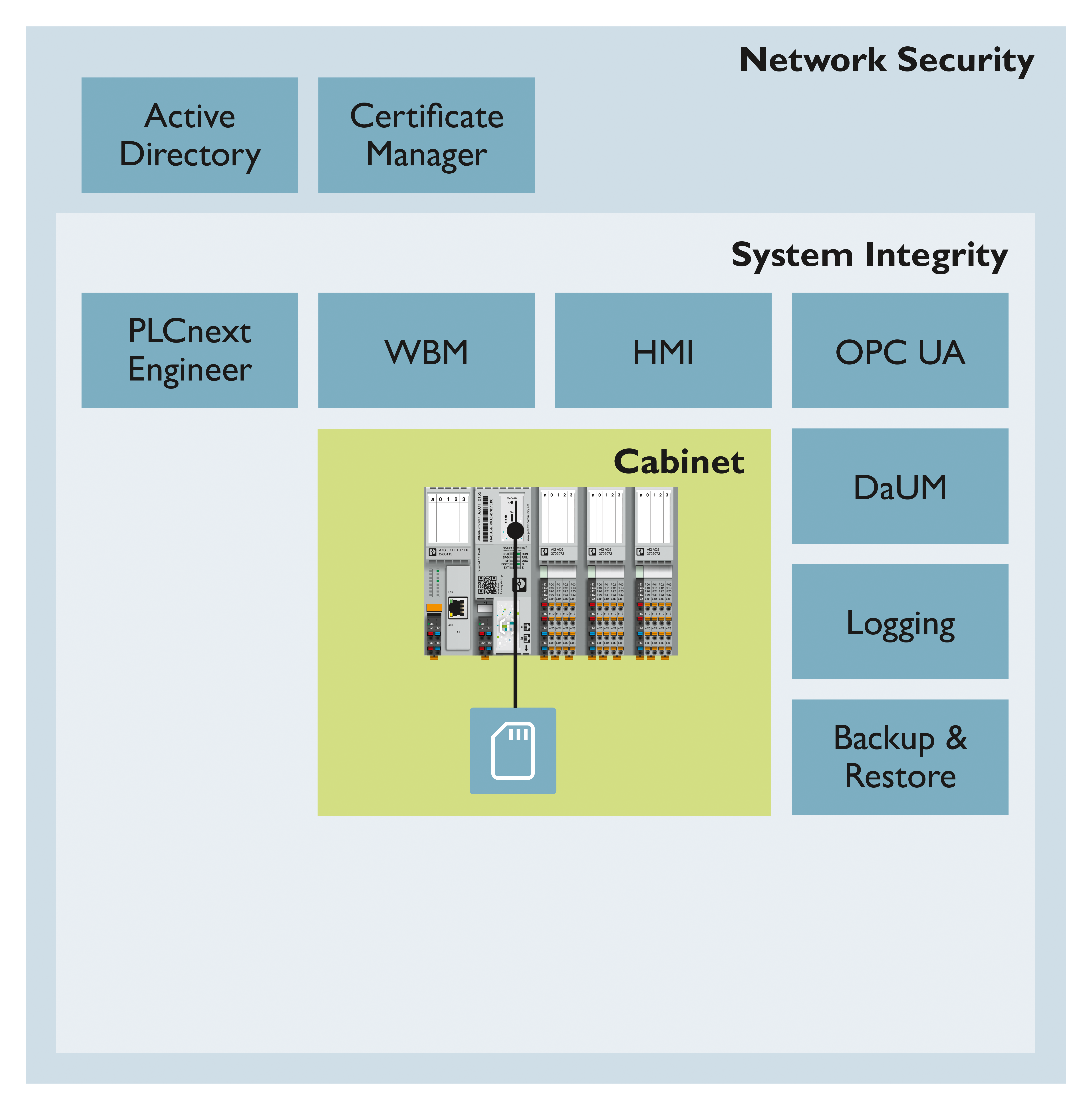
Security measures
Data in rest
PLCnext Technology’s data is stored on an internal (non-removable) SD card. The detailed description of the data and directory structure can be found in the main PLCnext Technology ‑ Info Center at the Directories of the firmware components.
The storage capacity of a PLCnext Control can be enhanced with an external (removable) SD card. Activating the Security Profile is deactivating the external SD card usage because additional security measures are needed to protect the external SD card against unauthorized physical access.
In addition to the extra space for automation project data, the external SD card enables an easy device replacement with licenses transferred via that storage medium. From firmware version 2022.0 LTS special SD cards are available supporting the distribution of licenses:
- SD FLASH 16GB PLCNEXT MEM LIC (item no. 1831737)
- SD FLASH 32GB PLCNEXT MEMORY LIC (item no. 1151111)
- SD FLASH PLCNEXT MEMORY LIC CFG (item no. 1308064)
- SD FLASH 8GB PLCNEXT MEMORY LIC (item no. 1151112) - discontinued
From firmware 2024.0 LTS, these special SD cards provide data protection, and therefore can be used together with the Security Profile.
For further information about protecting the sd card, refer to the topics Protection against physical access and Secure disposal and the topic of the respective controller (e.g. AXC F 2152 ).
Data in transmission
To support secure communication e.g. via TLS, different options of cryptographic keys can be can be configured in the Certificate Authentication WBM page.
- PLCnext Technology self-signed certificates are preconfigured for HTTPS and OPC UA®. Additional self-signed certificates can be configured according to the user’s needs.
- Certificates are installed from an asset owners PKI. To configure dedicated asset owner identities, keys and certificates generated by a PKI can be installed in the identity store on the PLCnext Control device.
- PLCnext supports TPM-generated keys and their related certificates. TPM-generated keys are currently usable for the TLS function block in the PLC application. Further use cases will be available in the future. TPM-generated keys are only valid in relationship with the dedicated TPM.
Use case 1 and 2 offer more flexibility for device replacement but less strict security as the private keys are stored in the PLCnext Control's file system. Additional system security measures might be needed to protect the device against physical access of the internal SD card.
Use case 3 offers high security as the private keys are not stored in the file system but the key generation is more complex. As well the device replacement is more complex because the keys are only valid on the device which contains the specific TPM which has generated the key.
User Management
PLCnext Technology’s User Management provides authentication and authorization on each communication interface. Only authorized users can access (read/write) data via a communication interface.
Software information integrity and authenticity
Software information security is provided by different mechanisms:
- Boot integrity check (software based partial; see Checking the integrity state )
- Signature of firmware container
- Each PLCnext Technology-related software provided for download from the Phoenix Contact website provides an SHA256 value. It can be used to check the integrity of the software after download before installation on the PC or on the PLCnext Control.
Mobile and malicious code protection
Authentication and authorization are provided by the User Management: Only authorized users get access (read/write) to the PLCnext Control's data.
PLCnext Engineer enforces the user to enter his credentials before accessing the controller. Only authorized users can download an application to the PLCnext Control device. An integrity check is performed in PLCnext Engineer (see Checking project data integrity ).
PLCnext Engineer or toolchains generating code must be installed on secure managed PCs only. In the security context, one especially supervised engineering PC is installed in the Manufacturing zone for engineering access to the PLCnext Control devices during maintenance phases.